Describes 802.1x or PNAC settings.
The 802.1X or PNAC ((the IEEE Standard
for port-based Network Access Control (PNAC))
provides an authentication mechanism to devices attached to a bridge
port. It prevents access to a port when the authentication fails. 802.1X defines port-based authentication
as a client-server based access control and authentication protocol
that restricts unauthorized clients from connecting to a LAN through
publicly accessible ports. An authentication server validates each
supplicant (client) connected to an authenticator (network access
switch) port before making available any services offered by the
switch or the LAN.
Until the authentication is provided, 802.1X access
control allows only EAPOL (Extensible
Authentication Protocol Over LAN) traffic through the port only
when the authentication is provided.
To access 802.1X screens, go to .
802.1X Basic Settings
By
default, the tab Global Settings displays
the LLDP Global Configuration screen.
Figure 1. 802.1X Basic Settings
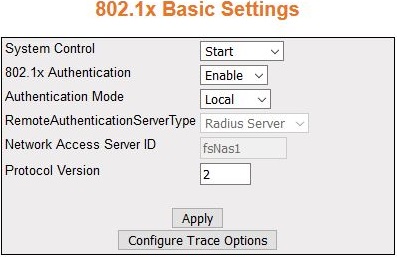
| Screen Objective |
This screen allows the user to configure Authentication
status, Authentication mode, and Authentication server type. |
| Navigation |
|
| Fields |
- System Control—select
the system control status of the PNAC module.
The default option is Start. The options are:
- Start—starts PNAC Module in the system.
- Memory Resources required by PNAC module
are allocated and PNAC module
starts running.
- Creates Memory pool, generates the PNAC interface
task; initializes all global data structures.
- Creates a hash table for storing the session nodes for MAC based authorization
entries.
- Creates semaphore for controlling concurrent access to critical
databases
- Initializes the timer submodule and PNAC Local authentication
server module.
- Shutdown—shuts down PNAC Module.
- All resources used by PNAC module
are released to the system and the PNAC module
is shut down.
- Initializes all PNAC state
machines.
- Deactivates the PNAC Local
authentication server module, the timer module. Deletes the memory
pool for the PNAC module and
free its memory.
- Deletes semaphore used for database access-control.
- 802.1x Authentication—select the status
of 802.1X based port security
feature in the switch. The default option is Enable. The options
are:
- Enable—enables 802.1X based
port security feature in the switch. The switch initiates authentication
and sends an EAP-request/identity frame to the client to request
its identity (typically, the switch sends an initial identity/request
frame followed by one or more requests for authentication information).
Upon receipt of the frame, the client responds with an EAP-response/identity
frame.
- Disable—disables 802.1X based
port security feature in the switch. EAPOL frames
from the client are dropped. If the client does not receive an EAP-request/identity
frame after three attempts to start authentication, the client transmits
frames as if the port is in the authorized state.
- Authentication Mode—modifies attributes
and saves the changes.
- Remote—RADIUS server
based authentication. It calls the AS client
functions to communicate with the remote authentication server.
- Local—provides the authentication service requirements in the
local database. It maintains a simple database of users who can
be permitted on valid proof to access a set of Authenticator’s ports.
It calls the service functions of the Local AS.
|
| Fields (cont) |
- RemoteAuthenticationServerType—select
the Remote Authentication Server Type. The default option is RADIUS Server. The options are:
- RADIUS Server—sets the
remote authentication server as RADIUS Server. RADIUS server is responsible
for authentication, authorization and maintaining its account information
with port-based authentication. It is a gateway that controls access
to the network. RADIUS uses
the User Datagram Protocol (UDP). RADIUS server acts as the centralized
authentication server.
- Tacacs Server—sets the remote authentication server as TACACS Server. The remote TACACS+ server is responsible
for TACACS+ client communication
to authenticate the user, get authorization information, and send
accounting information to the user. TACACS+
uses the Transmission Control Protocol (TCP).
This feature is currently not supported.
Note: This field can
be configured only if the Authentication Mode is set as Local.
- Network Access Server ID—enter the Network
Access Server ID; it is the server ID for which authentication is
provided. The Authenticator ID originates from the Access Request
packets. The value is a string type.
- Protocol Version—specifies the Version
Number of the Protocol. This is a read-only field.
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
- Configure Trace Options—accesses the PNAC Traces screen.
|
PNAC Traces
Figure 2. PNAC Traces
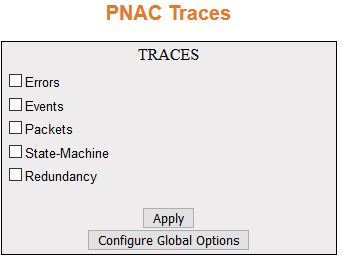
| Screen Objective |
This screen allows the user to enable the required
debug statements that are useful during debug operation. A four-byte
integer is used for enabling the level of tracing. Each BIT in the
four-byte integer represents a particular level of Trace. Combination
of levels is also allowed.
System errors such as memory allocation
failures are announced by means of LOG messages and TRACE messages.
Interface errors and protocol errors are made known by means of
TRACE messages.
|
| Navigation |
Click Configure
Trace Options
|
| Fields |
- Traces—select
the traces for which debug statements is to be generated. The default
option is critical. The options are:
- Errors—generates debug
statement for all failure traces of the below mentioned trace.
- Events—generates debug statements for event handling traces.
This trace is generated in case of event processing.
- Packets—generates debug statements for packets handling traces.
This trace is generated in case of transmission or reception of
packets.
- State-Machine—generates debug statements for state machine handling traces.
This trace is generated in case of State Machine processing.
- Redundancy—generates debug statements for redundancy code flow traces.
This trace is generated in case of redundancy processing.
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
- Configure Global Options—accesses the 802.1X Basic Settings screen.
|
802.1X Port Settings
Figure 3. 802.1X Port Settings
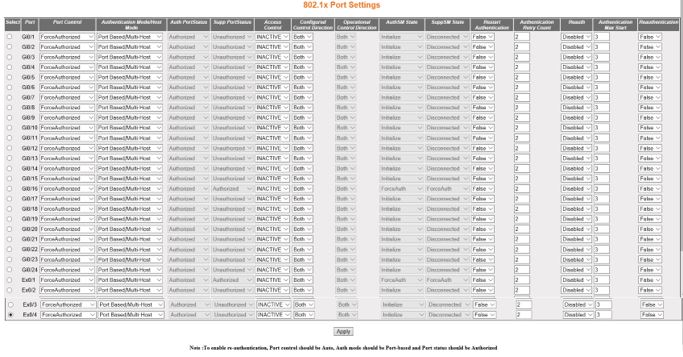
| Screen Objective |
This screen allows the user to configure the
security information at the individual port levels. |
| Navigation |
|
| Fields |
- Select—select
the port for which the configuration needs to be done.
- Port—displays the port, which is a combination
of interface type and interface ID. The interface ID is a combination
of slot number and the port number (slot number/port number).
- Port Control—select the control values
of the Authenticator Port. The default option is ForceAuthorized.
The options are:
- ForceAuthorized—allows all traffic through
this port; disables 802.1X authentication
and causes the port to transition to authorized state without requiring
authentication exchange. The port transmits and receives normal traffic
without 802.1X-based authentication
of the client.
- ForceUnauthorized—blocks all traffic through this port; causes
the port to remain in the unauthorized state, ignoring all attempts
by the client to authenticate. The switch cannot provide authentication
services to the client through the interface.
|
| Fields (cont) |
- Port Control—the
options are (cont):
- Auto—imposes 802.1X authentication
process in this port. Causes the port to begin the unauthorized
state, allowing only EAPOL frames
to be sent and received through the port. The authentication process
begins when the link state of the port transitions from down to
up or when an EAPOL-start frame is
received. The switch requests the identity of the client and begins
relaying authentication messages between the client and the authentication
server.
- Authentication Mode/Host Mode—select
the authentication mode to be imposed on the entry. The default
option is Port Based. The list contains:
- Port Based/Multi-Host—authenticates
and authorizes devices attached to a Bridge port that has point-to-point
connection characteristics named as Port based network access control.
The following occurs when Port Based authentication is selected:
- Receives incoming tagged / untagged data / control frames from
the CFA Module (Interface Manager) and checks if the Port is authorized. If
authorized, the frame is passed to the higher layer.
- Receives outgoing data/control frames from the other modules.
If authorized, the frame is passed to the CFA module.
- When an EAPOL frame is received from CFA, it sends the EAP packet
to the PNAC Interface Task, which then passes it to the Authenticator Module
or Supplicant Module.
- It forwards all received EAPOL-Start, EAPOL-Logoff and EAP-Responses to
the Authenticator Module via the PNAC Interface
Task.
- It forwards all received EAP-Requests, EAP-Success, and EAP-Failure
to the Supplicant Module via the PNAC Interface
Task. It forwards all received EAPOL-Key frames to the Key Handler
Module via the PNAC Interface Task.
- It maintains the physical link status information provided by
CFA and informs the Authenticator and Supplicant modules to take
the necessary action on physical link UP/DOWN conditions.
- It forms an EAPOL frame when requested by the Authenticator
Module or Supplicant Module or Key Handler Module and transmits
it to CFA
- Mac Based / Single-Host—authenticates and authorizes devices
attached to a Bridge port in the shared LAN named as MAC-based network access control.
The following occurs when MAC-based
authentication is selected.
- On receiving tagged/untagged
data/control frames from the CFA Module, it checks if the source MAC is present in the Authenticator Session
Table and if it is authorized.
- If it is present in the table and is authorized, the result
is passed to CFA, which then forwards the frame to the appropriate
destination module.
- If it is present in the table but not authorized, the CFA Module
is dejected, and the frame is dropped at the CFA Module.
|
| Fields (cont) |
- Authentication Mode/Host
Mode—the list contains (cont):
- Mac Based / Single-Host—(cont).
- If neither of the above occurs, the Authenticator will initiate
a new authentication session for that source MAC address
and return the unauthorized status to the CFA Module, which then
drops the frame.
Note: MAC based authentication can
be configured only if the Port control option is Auto.
- Auth Port Status—displays the status
of the Supplicant PAE state machine. The options are:
- Authorized—the
module is ready for transmission or reception of data.
- Unauthorized—the module is not ready for transmission or reception
of data.
- Supp Port Status—displays the status
of the Authenticator Port. The options are:
- Authorized—the
module is ready for transmission or reception of data.
- Unauthorized—the module is not ready for transmission or reception
of data.
- Access Control—select the Access Control
status for the port. This setting is for the application of the
Supplicant authorization state when the port is operating as both
Supplicant and Authenticator. The default option is INACTIVE. The
list contains:
- INACTIVE—indicates that the port uses only
the Authenticator authorization state to restrict access to the
port and not the Supplicant authorization state.
- ACTIVE—indicates that the port applies both the Supplicant authorization state
and Authenticator authorization state.
- Configured Control Direction—select the
value of the administrative controlled directions parameter for
the port. The options are:
- Both—authentication control is
imposed on both incoming and outgoing packets.
- In—authentication control is imposed on the incoming packets.
- Operational Control Direction—select
the value of the operational controlled directions parameter for
the port. The options are:
- Both—authentication control is
imposed on both incoming and outgoing packets.
- In—authentication control is imposed on the incoming packets.
|
| Fields (cont) |
- Auth SM State—select
the value of the operational controlled directions parameter for the
port. The options are:
- Initialize—this state occurs when
the module is disabled and port is down.
- Disconnected—there will be a transition from Initialize to disconnecting. State
Machine (SM) never remains in this
state—there will be an immediate transition.
- Connecting—this state is the beginning of the PNAC packet exchange.
- Authenticating—this state occurs whenever authenticator receives response
ID from supplicant.
- Authenticated—this state occurs whenever authenticator SM port transitions to authorized
through EAP exchange.
- Aborting—this state occurs when Authenticator SM receives re-authenticating event
or EAP start or supplicant log off.
- Held—this state occurs when authentication failure occurs due
to wrong user name or password.
- ForceAuth—this state occurs when the port control is changed
to force authorized.
- ForceUnauth—this state occurs when the port control is changed
to force unauthorized.
- SuppSMState—select the state of the Supplicant
State Machine (SM). The options are:
- Disconnected—there will be a transition from Initialize to disconnecting. State
Machine never remains in this state—there will be an immediate transition.
- Logoff—state Machine never remains in this state and there will
be an immediate transition to the other state.
- Connecting—this state is the beginning of the PNAC packet exchange.
- Authenticating—this state occurs whenever authenticator receives response
ID from supplicant.
- Authenticated—this state occurs whenever authenticator SM port transitions to authorized
through EAP exchange.
- Aborting—this state occurs when Authenticator SM receives re-authenticating event
or EAP start or supplicant log off.
- Held—this state occurs when authentication failure occurs due
to wrong user name or password.
- ForceAuth—this state occurs when the port control is changed
to force authorized.
- ForceUnauth—this state occurs when the port control is changed
to force unauthorized.
|
| Fields (cont) |
- Restart Authentication—select
the value of the administrative controlled directions parameter
for the port. The options are:
- Reauth—select the re-authentication mechanism
on the port. It re-authenticates the port without waiting for the
configured number of seconds between re-authentication attempts
and automatic re-authentication. The default option is Disabled.
The options are:
- Enabled—enables re-authentication on the
port.
- Disabled—disables re-authentication on the port.
- Authentication Max Start—enter the maximum
number of successive EAPOL-Start messages that will be sent before
the supplicant assumes that there is no authenticator present. This
value ranges from 1 to 65535. The default value is 3.
- Reauthentication—select the re-authentication
mechanism on the port. It re-authenticates the port without waiting
for the configured number of seconds between re-authentication attempts
and automatic re-authentication. The default value is False. The
list contains:
- True—enables re-authentication on the port.
- False—disables re-authentication on the port.
Note: To
enable re-authentication, Port control should be Auto, Auth mode
should be Port-based, and Port status should be Authorized.
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
|
802.1X Timer Configuration
Figure 4. 802.1X Timer Configuration
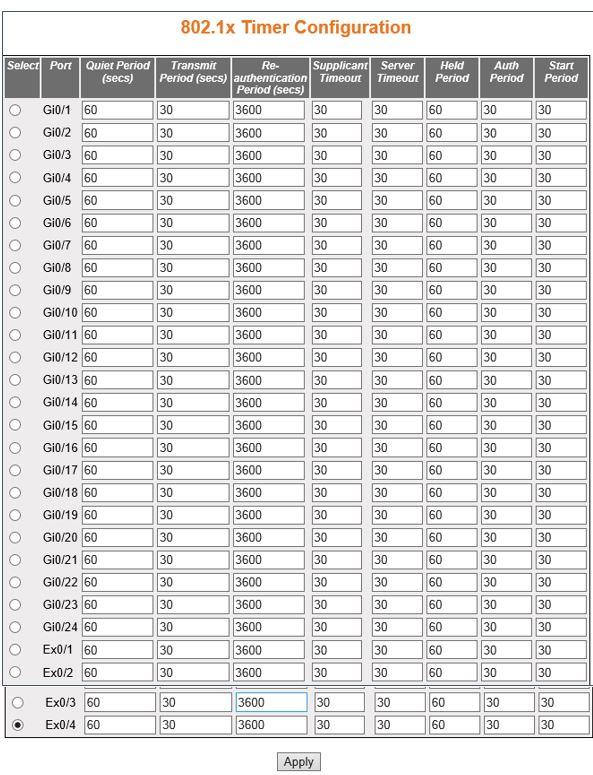
| Screen Objective |
This screen allows the user configure the Timer
parameters at the individual port level. |
| Navigation |
|
| Fields |
- Port—displays
the port, which is a combination of interface type and interface
ID. The interface ID is a combination of slot number and the port
number (slot number/port number).
- Quiet Period (secs)—enter the number
of seconds that the switch remains in quiet state following a failed
authentication exchange with the client. In this the duration the
authenticator remains silent and will not attempt to acquire a supplicant.
This value ranges from 0 to 65535 seconds. The default value is
60.
- Transmit Period (secs)—enter the Time
Period used by the Authenticator State machine to define when the
EAP Request ID PDU is to be transmitted.
This value ranges from 1 to 65535 seconds. The default value is
30.
- Re-authentication Period (secs)—enter
the time between periodic re-authentication of the supplicant. Re-authentication
period denotes the number of times the switch restarts the authentication
process before the port changes to the unauthorized state. This
value ranges from 1 to 65535 seconds. The default is 3600.
- Supplicant Timeout—enter the amount of
time the switch waits for a response before resending the request
to the client, when relaying a request from the authentication server
to the client. This value ranges from 1 to 65535 seconds. The default
value is 30.
- Server Timeout—enter the amount of time
the switch waits for a reply before resending the response to the
server, when relaying a response from the client to the authentication
server. This value ranges from 1 to 65535 seconds. The default value
is 30.
- Held Period—enter the amount of time
the client will wait before re-attempting a failed 802.1X authentication. When the
supplicant (in the client) receives an authentication failure indication
from the switch, it remains idle for a period of time which is determined
by the value of held-period. After this time, the supplicant initiates
authentication again. Authentication failure might occur if supplicant
provides a wrong password. This value ranges from 1 to 65535 seconds.
The default value is 60.
- Auth Period—enter the time interval for
resending 802.1X request messages
after not receiving a response. This value ranges from 1 to 65535
seconds. The default value is 30.
- Start Period—enter the time interval
for resending Start messages. Start period denotes the number of
seconds between successive EAPOL-Start messages following no response
from the authenticator. This value ranges from 1 to 65535 seconds.
The default value is 30.
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
|
Local Authentication
Server Configuration
Figure 5. Local Authentication Server Configuration
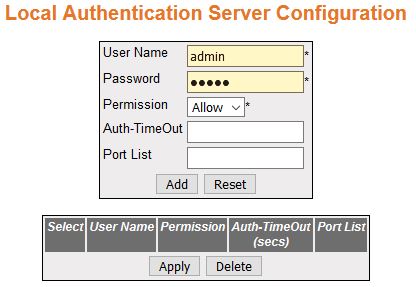
| Screen Objective |
This screen allows the user configure the local
Authentication Server (AS) information. It
contains authentication related user configuration information maintained
by PNAC local AS. Every entry contains user name,
password, authentication protocol used, authenticated session timeout,
and access ports list for an user seeking authentication. |
| Navigation |
|
| Fields |
- User Name—enter
the identity of the user seeking authentication. This field is a string
of maximum size 20.
- Password—enter the password specific
to the user name—a maximum size of 20.
- Permission—select the allowance /denial
of access for local authentication server. The options are:
- Allow—authentication
request is allowed for the set of ports in the Port List.
- Deny—authentication request is not allowed for the set of ports
in the Port List.
- Auth-TimeOut (secs)—enter the Authentication
Timeout in seconds. The time in seconds after which the Authentication
offered to the user ceases. When the object value is 0, the ReAuthPeriod
of the authenticator port is used by Authenticator. This value ranges
from 1 to 7200 seconds.
- Port List—enter the complete set of ports
of the authenticator to which the user is allowed or denied access,
based on the permission.
|
| Buttons |
- Add—adds and
saves new configuration.
- Reset—resets to default value for respective
fields and discards all user inputs.
- Apply—modifies attributes and saves the
changes.
- Delete—deletes the selected entry.
|
RADIUS Global Configuration
Figure 6. RADIUS
Global Configuration
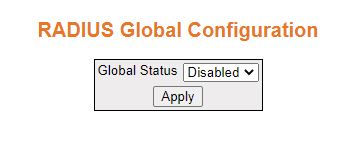
| Screen Objective |
This screen allows the user to enable the RADIUS Server. |
| Navigation |
|
| Fields |
- Global Status—select
enable or disable
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
|
RADIUS Server Configuration
Figure 7. RADIUS Server Configuration
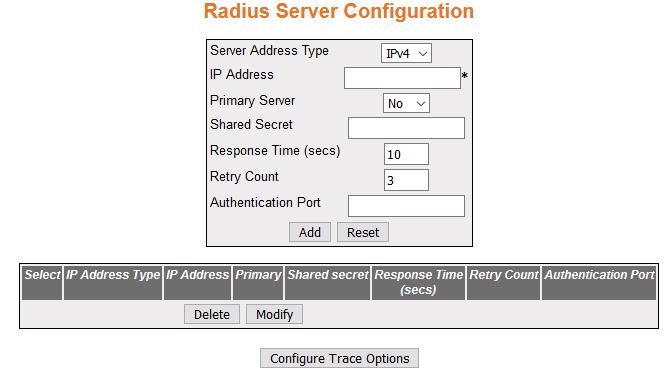
| Screen Objective |
This screen allows the user to configure the RADIUS Server settings. RADIUS (Remote Authentication
Dial-In User Service) is a portable implementation of the RADIUS client protocol. This
protocol carries authentication information between the Network Access
Server (NAS) that desires to authenticate its links and the RADIUS server that is responsible
for authenticating and maintaining the authentication information. |
| Navigation |
|
| Fields |
- Server Address Type—select
the RADIUS server address type.
The default option is IPv4, RADIUS server address type is set as
Internet Protocol Version 4, where a 32-bit address is used
- IP Address—enter the IP Address of the RADIUS Server.
- Primary Server—select a server type—a
primary server or not. Only one server can be configured as the
primary server. The default option is No. Options are:
- Yes—indicates
the server type as a primary server.
- No—indicates the server type is not a primary serve
- Shared Secret—enter the secret string,
which is to be shared between the RADIUS Server
and the RADIUS Client. The
shared secret is the secret of the server to which the request was
sent and from which the response was received.
- Response Time (secs)—enter the maximum
time within which the RADIUS Server is
expected to respond for a request from the RADIUS Client.
This value ranges from 1 to 120 seconds. The default value is 10.
|
| Fields (cont) |
- Retry Count—enter
the maximum number of times a request can be re-transmitted before
getting response from the RADIUS Server.
If the retransmit count has exceeded the configured maximum retransmissions,
the packet and the user entry are deleted from the user request
table and the error condition is logged. This value ranges from
1 to 254. The default value is 3.
- Authentication Port—enter the port number
used for authentication. This value ranges from 1 to 65535.
|
| Buttons |
- Add—adds and
saves new configuration.
- Reset—resets to default value for respective
fields and discards all user inputs.
- Apply—modifies attributes and saves the
changes.
- Delete—deletes the selected entry.
- Configure Trace Options—accesses RADIUS
Traces screen.
|
RADIUS Traces
Figure 8. RADIUS Traces
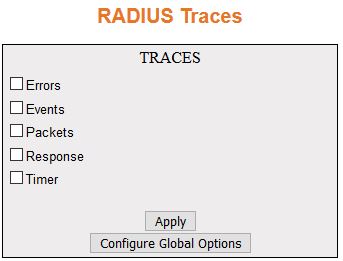
| Screen Objective |
This screen allows the user to enable the required
debug statements that are useful during debug operation. A four-byte
integer is used for enabling the level of tracing. Each BIT in the
four-byte integer represents a particular level of Trace. Combination
of levels is also allowed.
System errors such as memory allocation
failures are announced by means of LOG messages and TRACE messages.
Interface errors and protocol errors are made known by means of
TRACE messages
|
| Navigation |
Click Configure
Trace Options
|
| Fields |
- Traces—select
the traces for which debug statements is to be generated. The default
option is critical. The options are:
- Errors—generates debug
statement for all failure traces of the below mentioned traces
- Events—generates debug statements for event handling traces.
This trace is generated in case of event processing.
- Packets—generates debug statements for packets handling traces.
This trace is generated in case of transmission or reception of
packets.
- Response—generates debug statements for state machine handling
traces. This trace is generated in case of RADIUS processing.
- Timer—generates debug statements. This trace is generated for
timer functionality.
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
- Configure Global Options—return to the
RADIUS Server Configuration screen.
|
MAC Session Info
Figure 9. Mac Session Info

| Screen Objective |
This screen displays the MAC Session
information details. It contains authentication session information
associated with each Supplicant while the Authenticator operates in MAC-based authentication mode. The MAC session entries are deleted
from the port whenever it receives the port operational status down
information. |
| Navigation |
|
| Fields |
- Supplicant Mac Addr—displays
the Supplicant MAC Address for
the session.
- Session Identifier—displays the Session
Identifier of the supplicant.
- Auth SM State—select
the state of the Authenticator State Machine (SM)
for the entry. The list contains:
- Initialize—this state occurs
when the module is disabled, and port is down
- Disconnected—there will be a transition from Initialize to Disconnected. State
Machine never remains in this state and there will be an immediate transition.
- Connecting—this state is the beginning of the PNAC packet exchange.
- Authenticating—this state occurs whenever authenticator receives response
ID from supplicant.
|
| Fields (cont) |
- Auth SM State—the
list contains (cont):
- Authenticated—this state occurs whenever
authenticator SM port transitions
to authorized through EAP exchange.
- Aborting—this state occurs when Authenticator SM receives re-authenticating event
or EAP start or supplicant log off.
- Held—this state occurs when authentication failure occurs due
to wrong user name or password.
- ForceAuth—this state occurs when the port control is changed
to force authorized.
- ForceUnauth—this state occurs when the port control is changed
to force unauthorized.
- Auth Session Status—displays the Authentication
Session Status.
- authorized—the module is ready for transmission
or reception of data
- unauthorized—the module is not ready for transmission or reception
of data
- Session PortNumber—displays the port
number through which a particular Session MAC address is learnt.
- Session Initialize—select the Session
Initialize status for the Supplicant MAC Address
configured. The default value is True. This list contains:
- True—indicates
Session Initialize is set.
- False—indicates Session Initialize is reset.
- Session Reauthenticate—select the session
reauthentication status for the supplicant mac address configured.
The default value is True. This list contains:
- True—Indicates
session re-authentication is initialized.
- False—Indicates session re-authentication is reset.
|
| Buttons |
- Apply—modifies
attributes and saves the change.
|