This section describes how to configure the SSH protocol.
SSH (secure shell)
is a network protocol that allows data to be exchanged using a secure
channel between two networked devices. SSH uses
public-key cryptography to authenticate the remote computer and allows
the remote computer to authenticate the user, if necessary. SSH is typically used to log into
a remote machine and execute commands.
To access SSH screens, click .
SSH Global Settings
Figure 1. SSH Global Settings
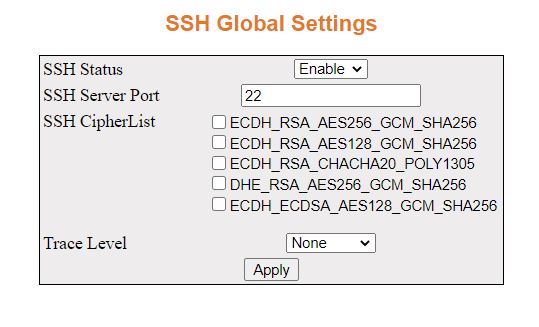
| Screen Objective |
This screen allows the user to configure the SSH initial settings. |
| Navigation |
|
| Fields |
- SSH Status—select
the status of the SSH module.
The default option is Enabled. The list contains:
- Enable—enables
the SSH feature in the switch. SSH feature enables the user to
log into a remote machine and execute commands.
- Disable—disables the SSH feature
in the switch. This action disconnects the secure channel.
- Version compatibility is set at Version 2 and cannot be changed.
|
| Fields |
- SSH CipherList—select
a Cipher-List. The cipher list takes values as bit mask. Setting
a bit indicates that the corresponding cipher-list will be used
for encryption. The default option is DES-CBC in NON-FIPS mode and
3DES-CBC in FIPS mode. The options are:
- ECDH_RSA_AES256_GCM_SHA256
- ECDH_RSA_AES128_GCM_SHA256
- ECDH_RSA_CHACHA20_POLY1305
- DHE_RSA_AES256_GCM_SHA256
- ECDH_ECDSA_AES128_GCM_SHA256
- Trace Level—this option enables debug logging at specific levels.
- None
- Warning
- Protocol
- Packet
- Functions
|
| Buttons |
- Apply—modifies
attributes and saves the changes.
|