This section describes how to configure a simple firewall.
This section will begin by enabling a simple firewall.
Once enabled, rules and complexity will be added as a means of providing
with a greater understanding of how to use the iMX950s firewall
capabilities.
For reference the network that will be used
for these exercises will be as shown:

- From a host on interface gig 0/2 you should be
able to ping a host on the network at gig 0/3
You should see som
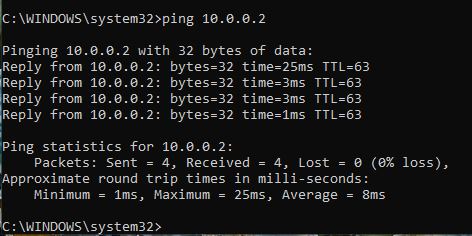
ething
similar to the following image:
- Enable the firewall.
- Navigate to Home > Layer 3 Management
> Security > Firewall > Global Configuration.
You will see a page similar to the following.
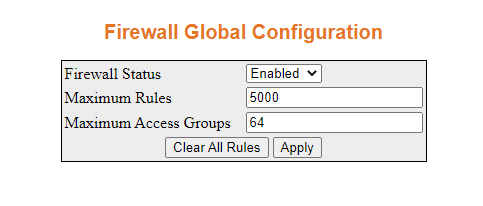
- Navigate to Home > Layer 3 Management >
Security > Firewall > Rule Configuration
You will see a page similar to the following:
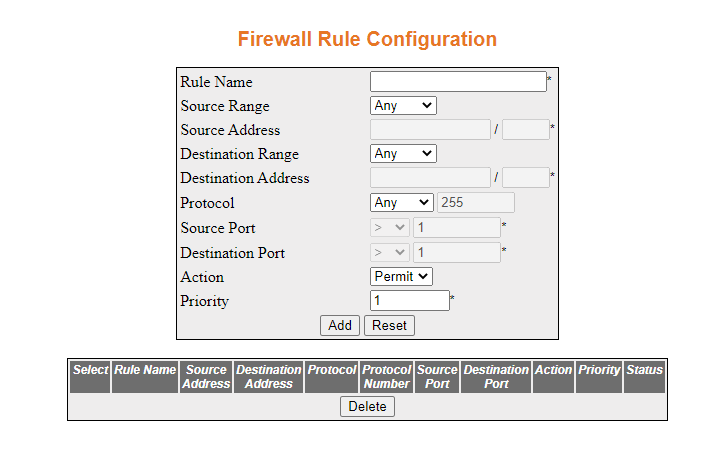
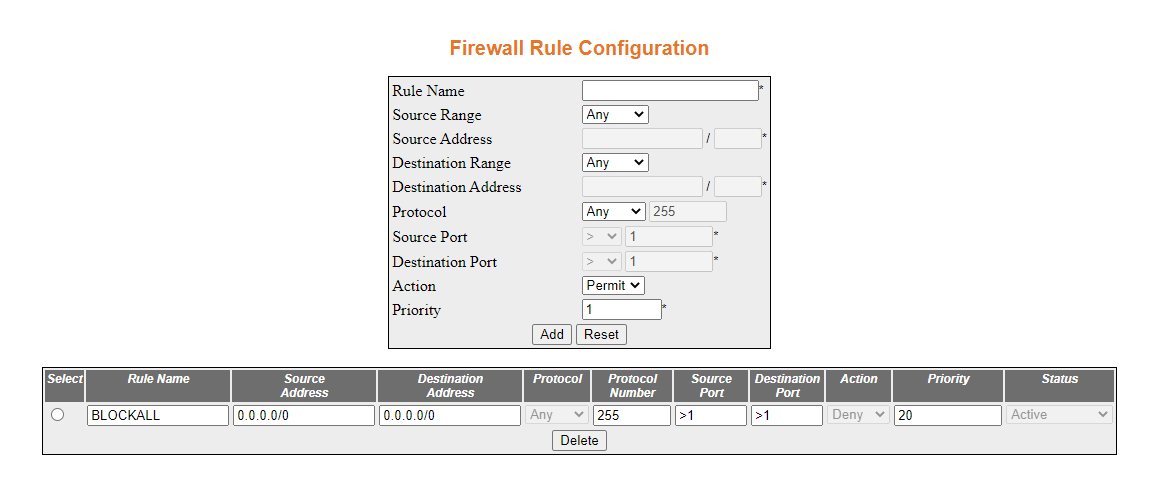
- Configure the firewall rule configuration as shown
below, and then click Add
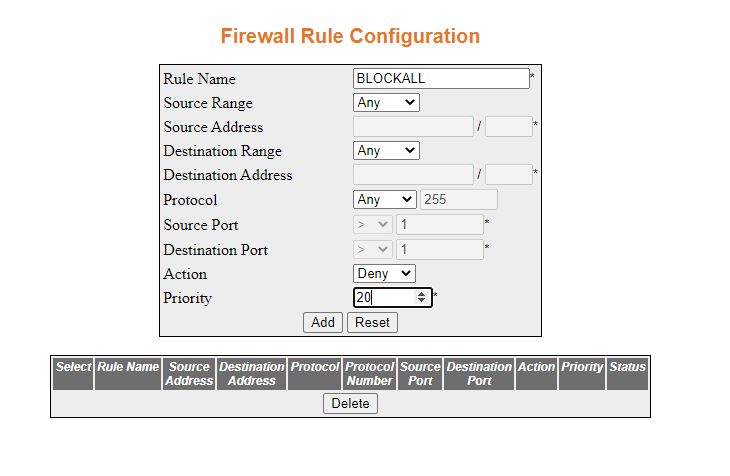
The rule will be added as shown below.
- Navigate to Home > Layer 3 Management >
Security > Firewall > Access Group Configuration
A page similar to the following will appear.

- Configure the access group as shown and then click Add.
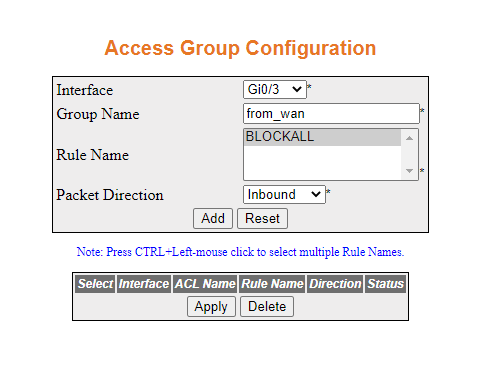
The following will appear.
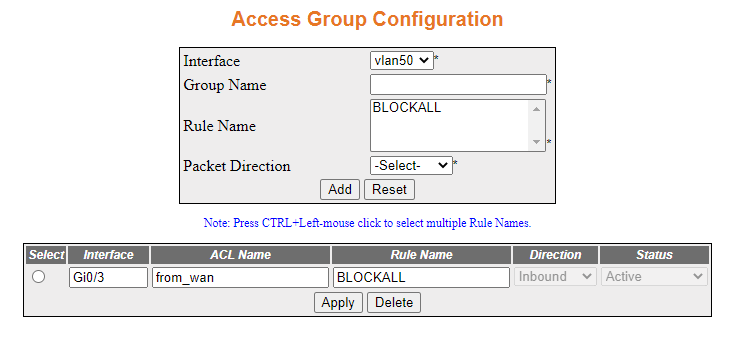
- Test the firewall from the
outside to the inside.
- Ping from the 10.0.0.0/8 subnet to 192.168.13.100
- Disable the firewall and repeat Step 3.
- Navigate to Home > Layer 3 Management
> Security > Firewall > Global Configuration. Change
the Firewall Status dropdown to Disabled and
then click Apply.
- Ping from the 10.0.0.0/8 subnet to 192.168.13.100
- Renable the firewall and verify that pings can pass from
the inside to the outside.
- Navigate to Home > Layer 3 Management
> Security > Firewall > Global Configuration. Change
the Firewall Status dropdown to Enabled and
then click Apply.
- Ping from the 192.168.13.0/24 subnet to
the 10.0.0.0/8 subnet
Note: The priority of the rules are important. As soon
as a packet is denied it will be discarded.
The lower the number
the higher the priority.
Add a rule to permit a host on the outside to ping the inside.
- Navigate to Home > Layer 3 Management
> Security > Firewall > Rule Configuration
The following screen will appear.

- Configure a rule as shown, then click Add

The rule will be created as shown.
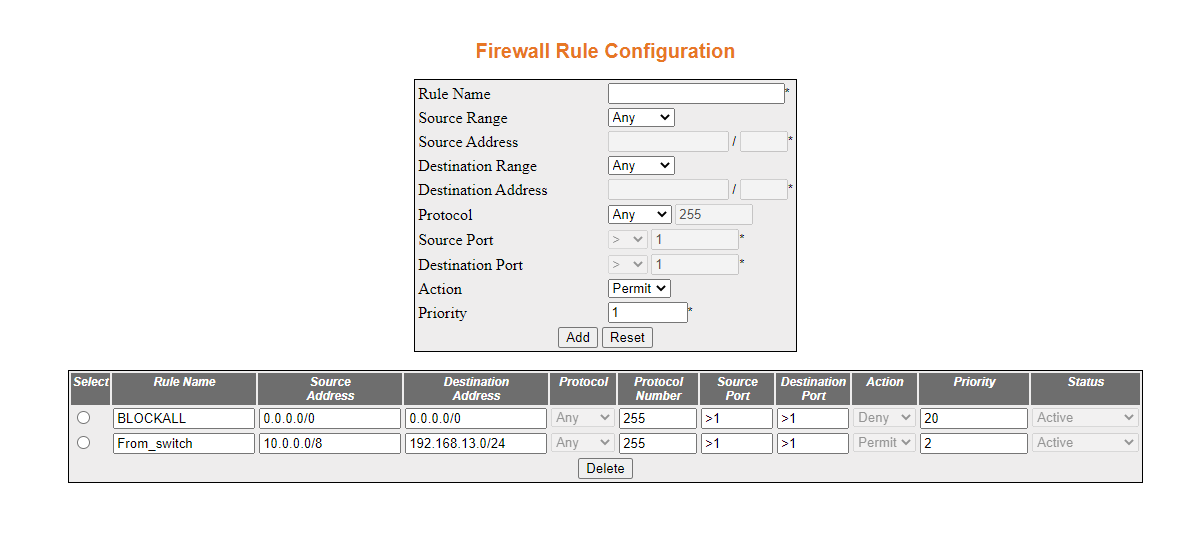
- Navigate to the Access Group Configuration,
select the row with interface Gi0/3 and in rule name type “From_switch,”
immediately before “BLOCKALL” as shown.
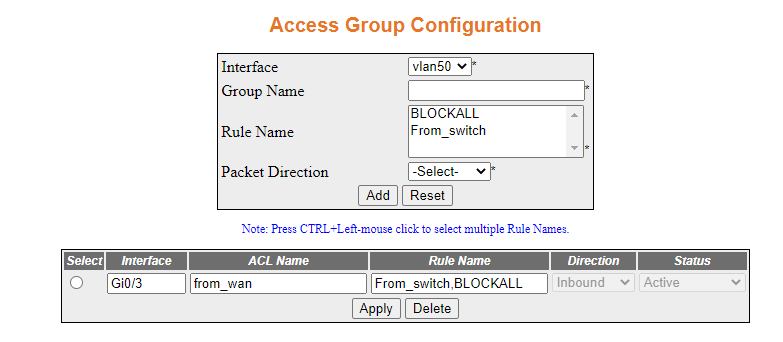
Then click Apply.
The rule will be added to the firewall.
- Ping from the host 10.0.0.2 can ping the 192.168.13.0/24
subnet.
The pings will be successful.
- Set up rules to allow the Inside to only access a single
HTTP address.
- Navigate to the Rule Configuration page.
Enter the following values shown below. Then click Add.
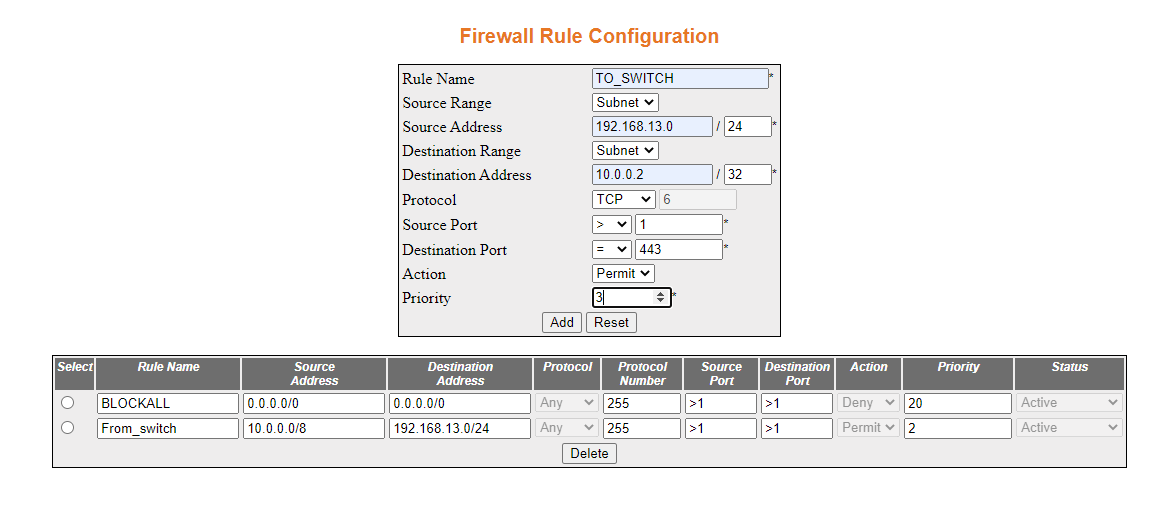
The rule will be created.
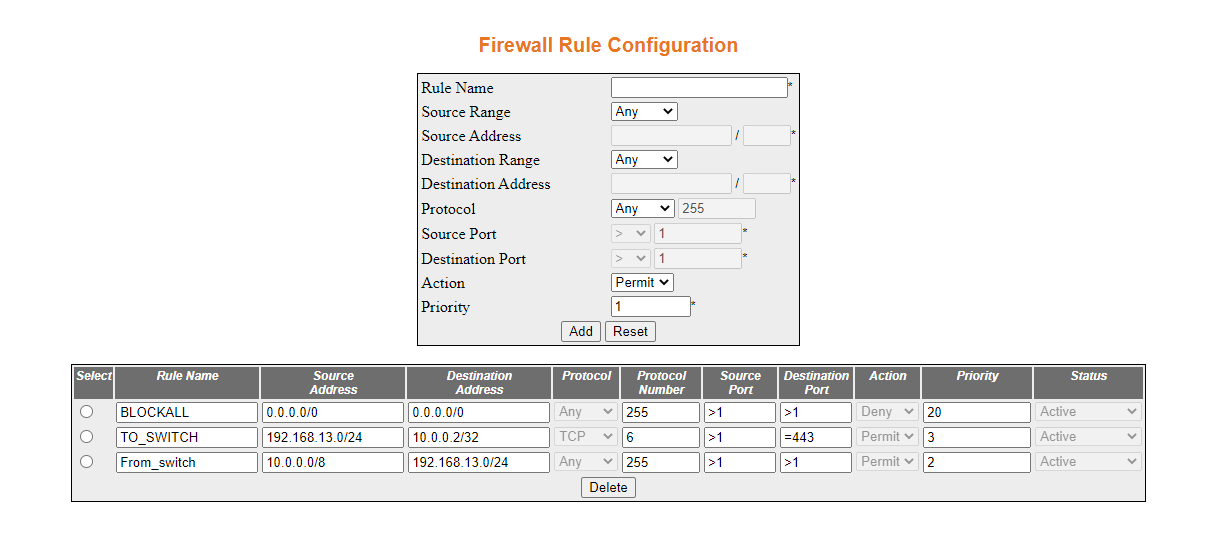
- Create an access group with the TO_SWITCH rule. Navigate
to Access Group Configuration. Populate
the fields and selections as shown below, then click Add.

The following screen will appear.

The rule has been configured.
- From a host on the 192.168.13.0/24 network ping a host
on the 10.0.0.0/8 network.
- From host 192.168.13.100 attempt to reach a web server
on 10.0.0.2.
Note: There is an assumption that there is a web server,
running on port 443 at 10.0.0.2 if not you may skip this step.
You will be able to reach the web server.
- To delete the firewall rules you created navigate to Home
> Layer 3 Management > Security > Firewall > Global Configuration. Click
on Clear All Rules.
You will receive a prompt to confirm your decision.
Once you click OK your firewall rules will
be deleted.
By the end of this section you will have successfully
done the following:
- Enabled a firewall
- Applied policies to inbound traffic
- Applied policies to outboud traffic
- Prioritized rules
- Are able to execute commands which show the state of the firewall