This section describes how to configure a simple firewall.
The steps needed to enable the iMX950 security
features must have been performed. This document assumes that the
steps listed in the Configuring the Security Application section
were performed.
This section will begin by enabling a simple firewall.
Once enabled, rules and complexity will be added as a means of providing
with a greater understanding of how to use the iMX950s firewall
capabilities.
For reference the network that will be used
for these exercises will be as shown:

- From a host on interface gig 0/2 you should be
able to ping a host on the network at gig 0/3
You should see som
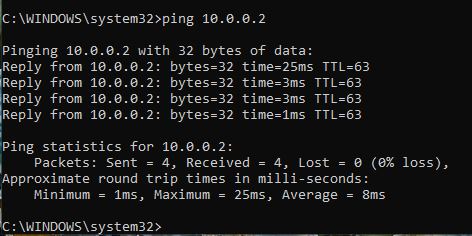
ething
similar to the following image:
- Enable the firewall.
- Execute the following commands:
iS5comm# configure terminal
iS5comm(config)#
firewall
iS5comm(config-firewall)# enable
iS5comm(config-firewall)#
rule BLOCKALL deny any any any priority 20
iS5comm(config-firewall)#
access-group from_wan in BLOCKALL interface gigabitethernet 0/3
iS5comm(config-firewall)#
exit
iS5comm(config)# exit
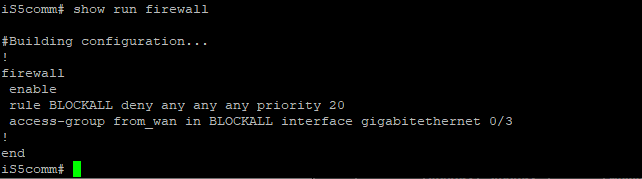
iS5comm# show run firewall
Text similar to the following will appear in the
terminal:
- Test the firewall from the
outside to the inside.
- Ping from the 10.0.0.0/8 subnet to 192.168.13.100
- Disable the firewall and repeat Step 3.
- Execute these commands
iS5comm# configure terminal
iS5comm(config)#
firewall
iS5comm(config-firewall)# disable
iS5comm(config-firewall)#
exit
iS5comm(config)# exit
- Ping from the 10.0.0.0/8 subnet to 192.168.13.100
- Renable the firewall and verify that pings can pass from
the inside to the outside.
- Execute these commands
iS5comm# configure terminal
iS5comm(config)#
firewall
iS5comm(config-firewall)# enable
iS5comm(config-firewall)#
exit
iS5comm(config)# exit
- Ping from the 10.0.0.0/8 subnet to 192.168.13.0/24
subnet
Note: The priority of the rules are important. As soon
as a packet is denied it will be discarded.
The lower the number
the higher the priority.
Add a rule to permit a host on the outside to ping the inside.
- Execute the following commands
iS5comm# configure terminal
iS5comm(config)#
firewall
iS5comm(config-firewall)# no access-group FROM_WAN
in
iS5comm(config-firewall)# rule FROM_SWITCH permit 10.0.0.2/32
any any priority 2
iS5comm(config-firewall)# access-group
FROM_WAN in FROM_SWITCH,BLOCKALL interface gigabitethernet 0/3
iS5comm(config-firewall)#
exit
iS5comm(config)# exit
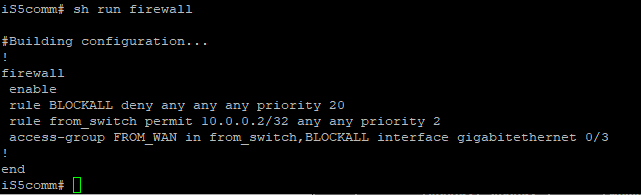
iS5comm#show running-config
firewall
Text similar to the following will appear:
- Ping from the host 10.0.0.2 can ping the 192.168.13.0/24
subnet.
The pings will be successful.
- Ping from any host on 10.0.0.0/8 except 10.0.0.2 to the
192.168.13.0/24 subnet.
- Set up rules to allow the Inside to only access a single
HTTP address.
iS5comm# configure terminal
iS5comm(config)#
firewall
iS5comm(config-firewall)# rule TO_SWITCH permit 192.168.13.100/32
10.0.0.2/32 tcp destport =80 priority 3
iS5comm(config-firewall)#
access-group FROM_PRIVATE out TO_SWITCH,BLOCKALL interface
gigabitethernet
0/3
iS5comm(config-firewall)# exit
iS5comm(config)#
exit
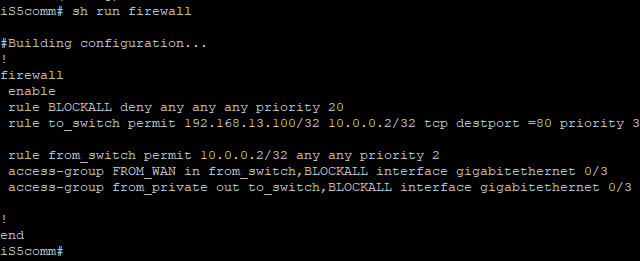
iS5comm# show running-config firewall
Text similar to the following will be on the terminal:
- From a host on the 10.0.0.0/24 network ping a host on
the 20.168.10.0/24 network.
- From host 10.0.0.1 attempt to reach a web server on 20.168.10.3.
Note: There is an assumption that there is a web server,
running on port 80 at 20.168.10.3, if not you may skip this step.
By the end of this section you will have successfully
done the following:
- Enabled a firewall
- Applied policies to inbound traffic
- Applied policies to outboud traffic
- Prioritized rules
- Are able to execute commands which show the state of the firewall